How to Tackle the Top SaaS Challenges of 2023
a call to action to join the upcoming webinar. The increasing rate of cyberattacks targeting SaaS applications has become a major concern for organizations in the digital age. These attacks have the potential to wreak havoc on businesses and steal valuable data. To ensure that businesses are adequately prepared to tackle the top SaaS challenges…
http://thehackernews.com/2023/02/how-to-use-ai-in-cybersecurity-and.html
Cybersecurity is a critical issue for businesses of all sizes, and the use of Artificial Intelligence (AI) is becoming increasingly popular as a way to detect, respond to, and prevent potential threats. AI has the potential to revolutionize the way businesses protect their data and networks from malicious actors. AI tools are being used in…
The Secret Vulnerability Finance Execs are Missing
a call-to-action. The financial services industry is one of the most targeted sectors when it comes to cyberattacks and breaches. The potential losses from cyberattacks could reach a few hundred billion dollars a year, eroding bank profits and potentially threatening financial stability. However, the risk goes beyond sophisticated APTs and cybercriminal operations. A vulnerability that…
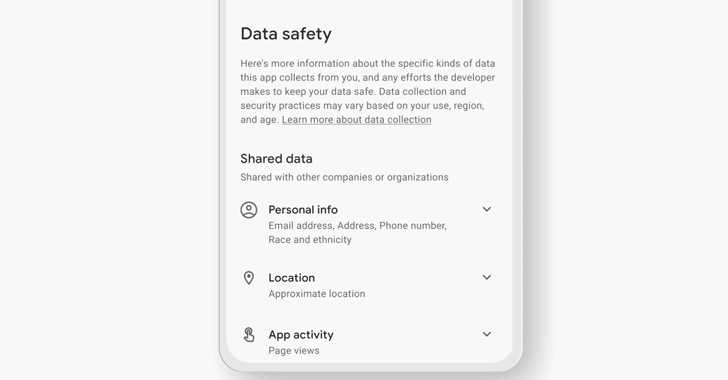
Investigation Reveals Serious Data Safety Label Loopholes in Google Play Store
Investigation Reveals Serious Data Safety Label Loopholes in Google Play Store A recent investigation conducted by the Mozilla Foundation under its “Privacy Not Included” initiative has exposed the existence of serious loopholes in data safety labels of Android apps available on the Google Play Store. The study compared the privacy policies and labels of the…