⚡Top Cybersecurity News Stories This Week — Cybersecurity Newsletter
Stay cyber-secure! This week’s cybersecurity newsletter covers interesting developments in the landscape and provides insightful analysis to help protect against potential threats. Here are the key points to take away: 1. Update Apple devices ASAP to fix a zero-day vulnerability being exploited by hackers. 2. ESXiArgs ransomware has been active for several months, targeting over…
How Does A VPN Enhance Your IT Security?
How Does A VPN Enhance Your IT Security? With the growing dependence on digital devices and the internet, cybersecurity has become a significant concern for individuals and businesses alike. Cybercriminals are continually finding new ways to exploit vulnerabilities and steal sensitive information, making it imperative to take measures to secure your online activity. One such…
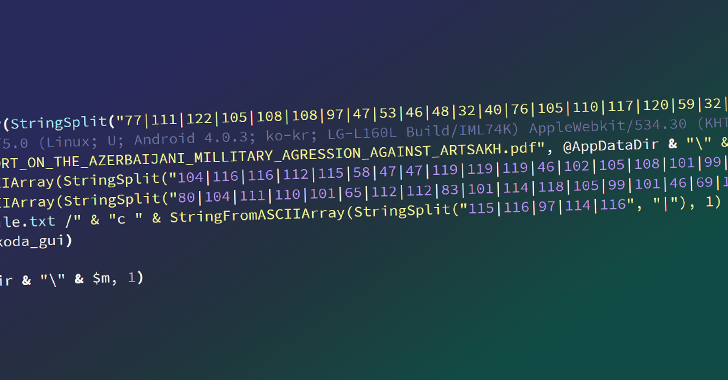
How to Detect New Threats via Suspicious Activities
How to Detect New Threats via Suspicious Activities Unknown malware presents a significant cybersecurity threat and can cause serious damage to organizations and individuals alike. When left undetected, malicious code can gain access to confidential information, corrupt data, and allow attackers to gain control of systems. To avoid these damaging circumstances, it is important to…