Researchers Share New Insights Into RIG Exploit Kit Malware’s Operations
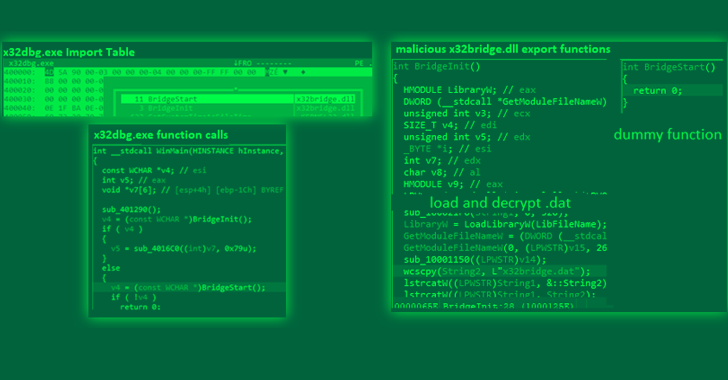
RIG Exploit Kit (EK) has become increasingly successful in exploiting vulnerabilities, reaching an all-time high successful exploitation rate of nearly 30% in 2022, according to new findings from the Swiss cybersecurity company PRODAFT. The kit is a financially-motivated program that has been active since 2014 and is used to distribute malware to large numbers of…