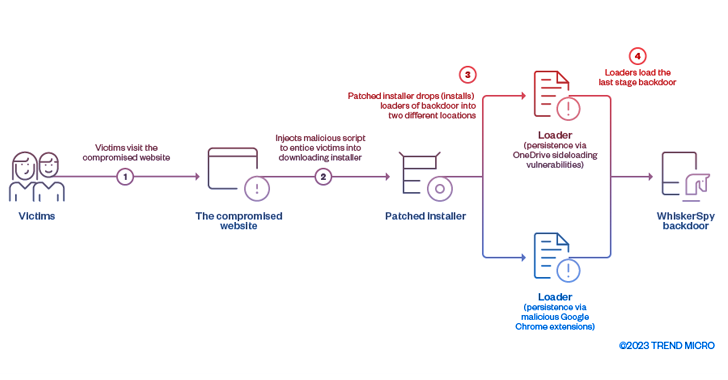
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. Earth Kitsune, active since at least 2019, is known to primarily target individuals interested in North Korea with self-developed malware such as dneSpy and agfSpy. Previously documented intrusions have entailed the use of watering holes that leverage browser exploits in Google Chrome and Internet Explorer to activate the infection chain. The differentiating factor in the latest attacks is a shift toward social engineering to trick users into visiting compromised websites related to North Korea, according to a new report from Trend Micro released last week.
The cybersecurity company said the website of an unnamed pro-North Korean organization was hacked and modified to distribute the WhiskerSpy implant. The compromise was discovered at the end of last year. When a targeted visitor tries to watch videos on the website, a malicious script injected by the attacker displays a message prompt notifying the victims with a video codec error to entice them to download and install a trojanized codec installer. The booby-trapped script is said to have been injected into the website’s video pages, with the installer (Codec-AVC1.msi) subsequently employed to load WhiskerSpy. But the attack also exhibits some clever tricks in an attempt to sidestep detection. This involves delivering the malicious script only to those visitors whose IP addresses match specific criteria – An IP address subnet located in Shenyang, China, a specific IP address located in Nagoya, Japan, and an IP address subnet located in Brazil.
Persistence is achieved by either abusing a Dynamic Library Link (DLL) hijacking vulnerability in OneDrive or via a malicious Google Chrome extension that employs native messaging APIs to execute the payload every time the web browser is launched. The WhiskerSpy backdoor, like other malware of its kind, comes with capabilities to delete, enumerate, download and upload files, take screenshots, inject shellcode, load arbitrary executables.
Earth Kitsune is not the only threat actor to go after Japanese targets, for the cybersecurity company also detailed another intrusion set codenamed Earth Yako striking research organizations and think tanks in the country. The activity, observed as recently as January 2023, is a continuation of a previously known campaign referred to as Operation RestyLink. A subset of the attacks also targeted entities located in Taiwan.
Earth Yako’s modus operandi is characterized by actively changing their targets and methods. The starting point is a spear-phishing email that masquerades as invitations to public events. The messages contain a malicious URL that points to a payload, which, in turn, is responsible for downloading the malware onto the system. The attacks are also characterized by a trove of custom tools comprising droppers (PULink), loaders (Dulload, MirrorKey), stagers (ShellBox), and backdoors (PlugBox, TransBox).
The exact origins of Earth Yako remain unknown, but Trend Micro said it identified partial technical overlaps between the group and other threat actors like Darkhotel, APT10 (aka Stone Panda), and APT29 (aka Cozy Bear or Nobelium).
Recent targeted attacks have shifted to targeting individuals considered to have relatively weak security measures compared to companies and other organizations. This shift is highlighted by the targeting and abuse of Dropbox as it is considered a popular service in the region among users for personal use, but not for organizations.
The cyber threat actor Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. The hacker group is known to primarily target individuals interested in North Korea with self-developed malware such as dneSpy and agfSpy. The latest attack involves a shift toward social engineering to trick users into visiting compromised websites related to North Korea. Additionally, a new threat actor, Earth Yako, has been identified as a continuation of a previously known campaign referred to as Operation RestyLink that is targeting research organizations and think tanks in Japan and Taiwan. The attacks are characterized by spear-phishing emails, custom tools, and backdoors such as PlugBox, ShellBox, and TransBox. Both Earth Kitsune and Earth Yako are actively changing their targets and methods and are targeting individuals with weak security measures. As such, it is important for individuals and organizations to be aware of the latest cyber threats and take the necessary steps to protect their systems and data.
Key Points:
• Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign.
• Earth Yako has been identified targeting research organizations and think tanks in Japan and Taiwan.
• Both Earth Kitsune and Earth Yako are actively changing their targets and methods and are targeting individuals with weak security measures.
• It is important for individuals and organizations to be aware of the latest cyber threats and take the necessary steps to protect their systems and data.